Introduction to Data Privacy Day
Data Privacy Day is an annual occasion of highlighting the vital need for protecting the personal information within the digital world. It is 28th January every year when everyone from individuals to organizations worldwide gathers together to raise the consciousness on data privacy. This article will cover such issues as changes in data privacy along with its relationship with data breaches, as well as emerging concepts of data privacy as a core human right.
Significance of Data Privacy Day
The purpose of Data Privacy Day is not only to remind people about their digital footprints but also make them get control over their online profiles. The volume of personal information we expose through different platforms demands a recognition of perils associated with our internet lives. By understanding what Data Privacy Day means, we can take early steps towards safeguarding our own data too.
The evolution of data privacy rights and regulations
When the Council of Europe first established European Data Protection Day in 2007, Data Privacy Day was born. 2009 saw the US Senate and House of Representatives adopt resolutions designating January 28 as National Data Privacy Day in recognition of its significance. Furthermore, it has been recognized by both Democrats and Republicans in the United States Congress as a national issue over the last two years.
Over the years there has been a remarkable shift in how data privacy is perceived and protected. Originally, privacy rights existed only for interactions offline. However, with proliferation of internet and exponential growth of digital data, there was need for strong privacy regulations. Consequently, governments and organizations throughout the world began to take measures to safeguard people from unlawful data collection and misuse.
Raising Awareness and Promoting Best Practices
Essentially, Data Privacy Day endeavors to increase sensitivity on issues pertaining to proper ways of maintaining confidentiality of information and data protection. It emerged in Europe and then spread across countries like USA, Canada, Qatar Nigeria Israel along with forty seven other European nations that feel its impact globally.
Data Privacy Day’s educational initiatives began with a focus on training businesses and users about safe cyber practices, especially within the realm of social networking. It includes fostering events and activities in support of technology tools development that promote individual control over personally identifiable information.
The Importance of Data Privacy
Defining data privacy and its impact, on individuals
Data privacy refers to the control that individuals have over the collection, use and sharing of their information. This includes data like records, medical history, browsing habits and social media activity. Failing to protect information can have consequences such as identity theft and damage to one’s reputation.
Investigating the extent of data
Any information that can identify or locate a specific person is considered data. This includes contact details like phone numbers and email addresses as important identifiers such as social security numbers and IP addresses. To fully understand the risks associated with exposure of data it is crucial to grasp the breadth of this type of information.
Recognizing the dangers of data breaches and misuse
Data breaches are becoming increasingly common. Can cause significant harm to individuals. These breaches expose information making people vulnerable to identity theft, financial fraud or even blackmail. Moreover unauthorized collection of data can be exploited for advertising purposes, manipulation tactics or even discriminatory practices.
Understanding the impact, on security and autonomy
When personal data falls into hands it compromises an individual’s independence and sense of security. Unauthorized access, to information can have consequences, including stalking, harassment and physical harm. Moreover, mishandling data can restrict an individual’s independence and control, over their life.
The role of data privacy in maintaining trust
Trust can only be built and maintained between individuals and organizations with the help of data privacy. Businesses are more likely to interact with customers who have confidence in the security of their personal data thus enabling them share their personal information over long periods.
Building trust between individuals and organizations
Organizations that prioritize user data privacy can build trust among their clients or users. Individuals who feel respected and appreciated are ready to transact or interact with organizations. This confidence is based on the promise that no one will use or abuse their personal data for any reason.
The relation between privacy and loyalty.
Loyalty from customers is directly dependent on how strong data privacy practices are. When people find an organization trustworthy and respectful of their information, they are more likely to remain loyal consumers’ Meanwhile, a breach of data or mismanagement of personal information can lead to loss of trust and consequently customer loyalty.
Improving data handling transparency and accountability
Data privacy supports transparency and accountability in the manner in which personal information is handled by organizations. Organizations can gain trust from individuals by clearly stating their practices of collecting and using data. This openness helps people in deciding whether to release their own personal information or not as well ensure that organizations face their responsibilities.
Data privacy as a basic human right
Data privacy is a fundamental human right recognized by nations worldwide. Several privacy laws have been formulated accompanied with international frameworks towards protection people from illegal surveillance and misuse of data.
Exploring privacy legislation and global frameworks
The laws, in place on Data Privacy Day were established to safeguard the privacy rights of individuals. The Treaty for the Protection of Individuals in relation to Automatic Processing of Personal Data initiated by the Council of Europe in 1981 is currently undergoing updates to address challenges posed by advancements. Additionally the Convention on Cybercrime plays a role in securing data systems. Ensuring privacy online. Furthermore Article 8 of the European Convention on Human Rights guarantees privacy as a right including data protection.
The General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) along with legislations have created data privacy regulations. These laws impose obligations on businesses regarding data protection, consent and individual rights. Furthermore, privacy is considered a human right under conventions like the European Convention on Human Rights and the Universal Declaration of Human Rights.
Protecting individuals from Surveillance and Data Abuse
Through data privacy laws, governments seek to protect people from surveillance and misuse of their information by private companies. Such regulations also require that personal information be collected in an informed and voluntary manner and used within specific defined limits. It guarantees a balance between individual’s privacy and society’s legitimate interest.
Balancing Privacy Rights against Needs of Society and Technology
It is important to note that as much as data privacy is important, there should be a tradeoff between privacy rights and society needs. Technological progress often encourages the collection and processing of personal information for service enhancement or development purposes. Striking this balance requires sensitive deliberation as well as systemic mechanisms for curbing misuse of personal data.
Ensuring Personal Information Security in the Digital Era
Best practices must be put into place to guarantee that our personal information remains safe during this digital age. Let us now examine some effective measures aimed at protecting our digital footprints.
Best Practices for Protecting Personal Information
Having strong and unique passwords
The initial line of defense against unauthorized access is passwords. When they are strong, it becomes very difficult to guess or crack them because they include uppercase and lowercase letters, numbers as well as special characters making them much stronger. As a result, single breach would not compromise multiple accounts in case this is prevented by having different passwords for different platforms.
Emphasizing security through two-factor authentication
An extra level of security is added on by two-factor authentication (2FA) which requires users to provide an additional verification code or fingerprint scan apart from just their password. So even after someone has succeeded to acquire your password, he will still need the physical access or knowledge of your second mode of authentication.
Proper handling and disposal of sensitive data
To keep privacy intact, sensitive data should be managed properly. This implies that secure storage should be maintained for documents and files containing sensitive information; encryption should be used when possible and important files must be regularly backed up. Additionally, it is important to either shred or delete permanently disposing physical or digital files so as to prevent any unauthorized entry to them.
Understanding the importance of encryption
Encryption plays a role, in safeguarding our data from access. By using algorithms to scramble information encryption ensures that authorized individuals can decipher the data. Understanding how encryption works and its application in data protection is vital for keeping information safe.
Explaining the principles of encryption and its role in protecting data
Encryption involves converting data, known as plaintext into a format called ciphertext. This transformation occurs through the utilization of algorithms and a unique encryption key. Without the key decrypting the ciphertext and accessing the information becomes extremely difficult.
The advantages and challenges of end-to-end encryption
End to end encryption (E2EE) is a method that guarantees data remains encrypted throughout its journey from sender to recipient with only that intended being able to decrypt and access the information. E2EE provides protection against interception but can present usability and maintenance challenges for users.
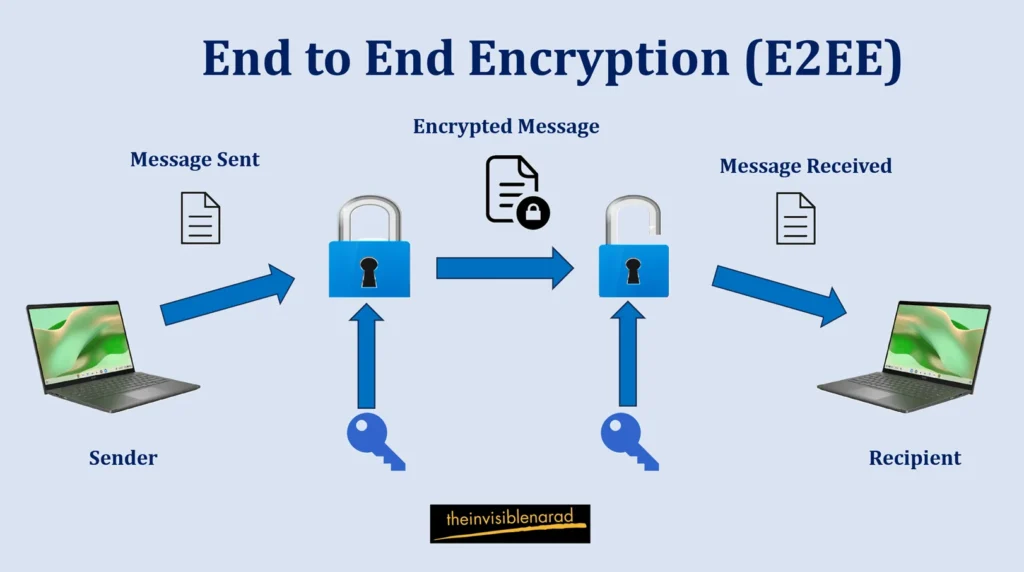
Identifying tools and practices for communication through encryption
Tools and practices are available to secure communication channels using encryption methods. Secure messaging applications such, as Signal and WhatsApp utilize encryption to ensure the security of our conversations. Likewise, when we use encryption tools like Pretty Good Privacy (PGP) to encrypt our emails we can be confident that only the intended recipient will be able to read the message.
Navigating platforms and privacy settings
When engaging with platforms it is crucial to be mindful of our privacy settings and take necessary precautions to safeguard our personal information.
Managing privacy settings on social media platforms
When it comes to media it is important to consider our privacy settings. By adjusting these settings we can have control, over who can view our profile, posts and personal information. It is essential to review and update these settings in order to maintain the desired level of privacy.
Managing app permissions and limiting data sharing
Apps often request access to permissions on our devices like contacts, location and camera. It’s important to review these permissions and only grant access when. Additionally being cautious about sharing data with third party apps helps prevent collection or misuse of information.
Understanding the implications of Wi-Fi networks and online tracking
Using Wi Fi networks can pose significant privacy risks as they are prone to exploitation by hackers. It is advisable not to access information such as banking or email accounts while connected to public Wi Fi. Also being aware of tracking methods like cookies and ad trackers empowers users to make decisions, about their digital presence.
Responsibility of Organizations in Ensuring Data Privacy
Securing data privacy extends beyond efforts. Organizations have a role to play in safeguarding information and fostering a culture of privacy within their operations. The success of Data Privacy Day owes a lot to the efforts of participating organizations. Institutions like the Anti Phishing Working Group, Carnegie Mellon University and the Federal Trade Commission (FTC) contribute to its advocacy initiatives ensuring an approach to data privacy and protection.
Fostering a Culture of Privacy within Organizations
Promoting Awareness about Privacy among Employees
Organizations must prioritize privacy education. Ensure that employees are well informed about practices. Regular training sessions on privacy awareness and awareness campaigns can help employees understand the significance of protecting data and the potential risks associated with a lack of privacy.
Establishing Transparent Data Privacy Policies
Clear and transparent data privacy policies provide guidelines for employees while building trust with customers. These policies should outline how personal data is collected, managed, protected, as highlight individuals rights concerning their own data. By developing comprehensive policies organizations demonstrate their commitment, to preserving data privacy.
Conducting Regular Privacy Audits and Risk Assessments
Regular privacy audits and risk assessments assist organizations in identifying vulnerabilities while evaluating their practices for safeguarding data. Through comprehensive assessments organizations can pinpoint areas that need enhancement and take the steps to bolster data privacy.
Complying with data protection regulations
Data protection laws such, as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) exist to protect the privacy of individuals data. It is essential for organizations to become acquainted with these regulations and ensure that they comply with them to avoid facing penalties.
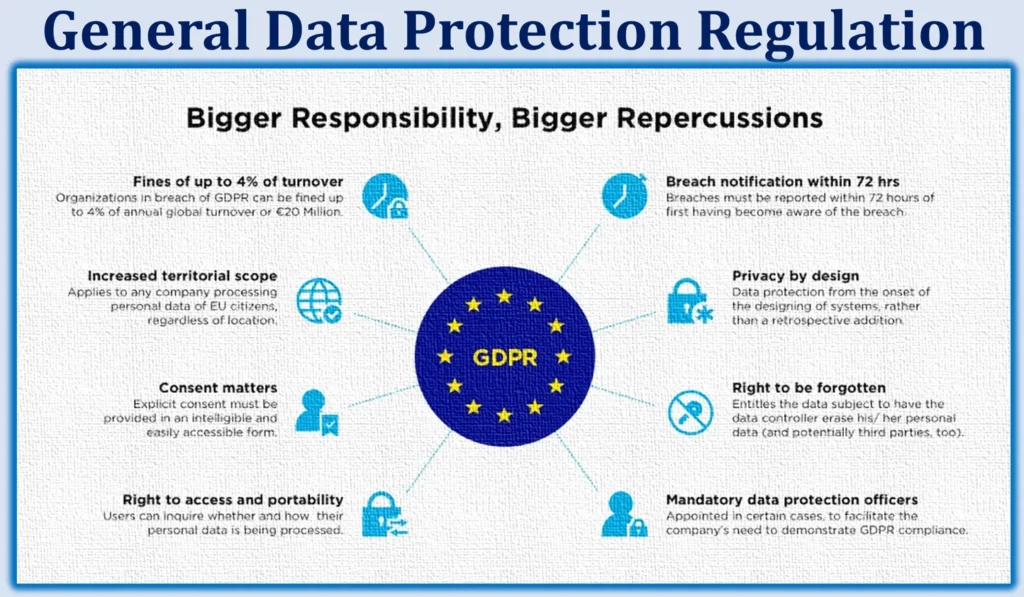
Getting acquainted with privacy laws (GDPR, CCPA, etc.)
Privacy laws play a role in protecting individuals data on a scale. By understanding the requirements laid out in these laws organizations can establish data protection practices. Steer clear of any non compliance issues.
Understanding the rights of data subjects and consent requirements
Data subjects hold rights when it comes to how their personal information’s collected, used and stored. Organizations need to grasp these rights and implement procedures that enable them to obtain consent from individuals before collecting or processing their data.
Mitigating financial risks associated with compliance
Neglecting adherence to data protection regulations can expose organizations to substantial legal and financial risks. Establishing processes and mechanisms becomes crucial for mitigating these risks; this includes appointing data protection officers as well as conducting privacy impact assessments, for new projects.
The role of technology in data protection
Technology can both enhance and pose challenges to data protection. Implementing certain technological practices and exploring emerging technologies can strengthen data privacy efforts within organizations.
Implementing the principles of privacy by design
Privacy by design emphasizes the integration of privacy features, into technology and systems from the beginning stages of development. By considering privacy considerations throughout the design process organizations can create products and services that prioritize privacy.
Exploring technologies for safeguarding data privacy (blockchain)
New technologies like blockchain hold promise in addressing challenges related to data privacy. Blockchain technology enables proof storage of data ensuring heightened security and privacy. Exploring how these technologies can be applied helps organizations establish ways to protect data.
Enhancing data protection practices through encryption and anonymization
Continually strengthening data protection practices is crucially important. Techniques like encryption and anonymization can enhance the security and privacy of information. By encrypting data both at rest and during transmission as anonymizing personally identifiable information (PII) organizations can minimize the risk of unauthorized access or data breaches.
“Data privacy isn’t simply a term – it’s a right that demands our active protection. By taking steps to safeguard our presence we can ensure that our personal information remains secure in the digital world.”
Data Privacy: Challenges and Solutions
In todays era, where technology has seamlessly integrated into our lives ensuring the security of our digital presence has become increasingly crucial. As we commemorate Data Privacy Day let us delve into the obstacles and remedies concerning data privacy.
Emerging threats to data privacy
Deepfake technology and identity theft risks
The rise of deepfake technology, in years has raised concerns about protecting our data privacy. Deepfakes, which are synthetic media content created using AI can be used to manipulate and impersonate individuals. This not puts our information at risk but also undermines trust in various sectors like politics and journalism. To safeguard ourselves from threats it’s crucial to implement authentication methods and raise awareness about the potential dangers of deepfakes.

Ethical concerns surrounding data monetization
The monetization of data, on platforms has become a business but it also raises ethical concerns regarding the use and exploitation of personal information. It’s important to establish regulations and guidelines that safeguard individuals privacy while still allowing innovation driven by data. By striking the balance we can foster an transparent digital economy.
Boundaries of data privacy in the era of Internet of Things
With the expansion of the Internet of Things (IoT) our everyday devices are becoming interconnected generating and exchanging amounts of data. While this interconnectedness brings convenience and efficiency it also pushes the boundaries of data privacy. To make sure our devices are secure, and our data remains protected from access it is crucial to prioritize encryption establish security protocols and raise user awareness.
Advancing data privacy through collaboration
In order to tackle the issues surrounding data privacy it is vital for stakeholders to collaborate. Here are three important areas where collaboration can strengthen data privacy:
Encouraging partnerships, between private sectors to tackle privacy challenges
By bringing together government agencies, private organizations and civil society we can combine resources, exchange knowledge. Create comprehensive strategies to address the challenges posed by data privacy. These collaborations have the potential to result in laws improved data protection practices and increased awareness.
Promoting cooperation in safeguarding data privacy
Data privacy concerns transcend borders. To effectively protect our information it is essential for organizations and governments to collaborate and harmonize policies. This collaborative effort aims to establish frameworks that not safeguard user privacy but also facilitate secure cross border data transfers for legitimate purposes. Such cooperation fosters trust among nations while ensuring the flow of data with safeguards.
Cultivating research and innovation for enhancing privacy measures
The evolving nature of technology necessitates ongoing research and innovation to proactively address privacy threats. Collaborations among computer scientists, legal experts, ethicists and policymakers can play a role in creating solutions for the challenges posed by data privacy. These interdisciplinary efforts encompass advancements in technologies that preserve privacy as frameworks, for evaluating the ethical implications of utilizing data. All contributing towards shaping the future landscape of data privacy.
Empowering individuals in data privacy decisions
As individuals, we hold the power to protect our own data. Here are three ways we can empower ourselves to make informed decisions about data privacy:
Privacy literacy enhancement and digital education
It is important that people are made aware of their data privacy rights and the possible risks they may face. Therefore, privacy literacy ought to be part of the curricula in schools and digital literacy programs. This can help mitigate data privacy risks by arming individuals with knowledge on how to safely navigate through the digital world.
Enhancing control over personal information for individuals
Tech companies need to prioritize giving people strong privacy controls and clear data management tools. Regaining trust and control over personal information necessitates that users become able to appreciate the ways in which their data is collected, used or shared. In this regard, well-articulated permission settings, user-friendly opt-out choices as well as simple privacy policies could be helpful.
Discussion on informed consent in relation to data protection laws and policies
Data privacy does not only relate to personal issues, but it also extends to societal ones. Participating in conversations concerning robust privacy laws as well as policy can make a difference. By participating in public forums, supporting privacy-focused organizations, and staying informed about legislative developments, we can shape the future of data privacy and protect our digital footprints.
Summary and FAQs
- Deepfake technology and identity theft risks are a tremendous challenge for data privacy.
- Ethical considerations with respect to data monetization must be addressed to support responsible data use.
- Data privacy boundaries have to be redrawn in the era of IoT.
- For data privacy to advance, stakeholders need to collaborate.
- Essential among these is international cooperation, partnerships between public and private bodies as well as interdisciplinary research.
- Through privacy education, personal data control and engaging in conversation about personal information protection rights and policies individuals can empower themselves.
As we ahead, it is clear that safeguarding our digital footprint is a collective responsibility By addressing emerging threats, advancing collaboration, and empowering individuals, we can ensure a future where data privacy is respected and protected. Let’s embrace this responsibility and towards a digital landscape that prioritizes privacy, trust, and individual rights.
“Data privacy is a matter that does not concern only an individual but the entire society. By taking proactive measures to safeguard our digital footprints we will be protecting our own interests and defending privacy as a basic right.”
Frequently Asked Questions (FAQs)
What is considered personal data?
Any information that may be used to identify a person, either directly or indirectly, is considered personal data. This includes names, addresses, phone numbers, email addresses, social media posts, IP addresses, and biometric data.
How can I protect my personal information online?
In order to safeguard your private data on the internet, you can:
1. Use strong and unique passwords for each account.
2. Enable two-factor authentication where possible.
3. Regularly update your devices and applications.
4. Use reputable antivirus and antimalware software.
5. Streer clear of downloading unfamiliar files or clicking on dubious links.
6. Share your personal information on social media with caution.What are the consequences of data breaches and identity theft?
Data breaches and identity theft can have severe consequences, including:
1. Financial loss due to fraudulent transactions.
2. Damage to personal and professional reputation.
3. Mental health problems and emotional suffering.
4. Potential legal and regulatory consequences.
5. Loss of trust in institutions and digital platforms.
