
The digital realm harbors a hidden underbelly known as the dark web, a mysterious domain inaccessible to conventional browsers. Beneath the surface lies a clandestine network where anonymity reigns supreme, fostering both illicit activities and legitimate endeavors. In this blog post, we will delve into the intricacies of this hidden corner of the internet, shedding light on its nuances and evolution.
Dark Web
Definition and its significance
The dark web is a collection of websites and online platforms that are intentionally hidden from search engines. Unlike the surface web, which is easily accessible and indexed by search engines, the dark web intentionally hides its content from conventional browsers and search engines. Websites on the dark web have addresses that end in “.onion” and are not accessible through standard browsers like Chrome or Firefox. Therefore they require special tools, such as the Tor browser, to access. It is significant due to its reputation as a haven for illegal activities, including the sale of drugs, weapons, stolen data, and illicit services. However, it also serves as a platform for whistleblowers, journalists, and individuals seeking privacy and anonymity for legitimate purposes.
Access to the dark web requires specialized software such as Tor (The Onion Router), I2P (Invisible Internet Project), or Freenet. These tools route internet traffic through a series of encrypted relays, masking users’ IP addresses and making it difficult to trace their online activities.
One of the primary distinguishing features of it is the emphasis on anonymity and privacy. Users can access content and communicate with others without revealing their identities, fostering an environment where individuals can engage in activities with reduced fear of surveillance or identification.
The Evolution of the Dark Web
Originally developed by the US Naval Research Laboratory for secure government communications, the Tor network became accessible to the public in the early 2000s, laying the groundwork for the dark web. Over time, it has evolved into a complex ecosystem, with various overlay networks like Tor, I2P, and Freenet offering different levels of anonymity and security. Its evolution has been shaped by technological advancements, law enforcement efforts, and changing societal attitudes towards online privacy and security.
How the dark web operates on overlay networks like Tor, I2P, and Freenet
- Tor (The Onion Router): Tor is one of the most widely used networks for accessing it. It operates by routing internet traffic through a series of volunteer-operated servers, known as nodes or relays. Each relay in the network only knows the IP address of the node that sent the traffic and the IP address of the node to which it should forward the traffic, preserving the anonymity of users.
- I2P (Invisible Internet Project): I2P is another overlay network that allows for anonymous communication and browsing. It uses a distributed, peer-to-peer architecture to create a network layer that is resistant to censorship and surveillance. Unlike Tor, I2P is designed to facilitate both anonymous web browsing and the hosting of hidden services.
- Freenet: Freenet is a decentralized network that prioritizes censorship resistance and content availability. It operates by storing encrypted data on distributed nodes, making it difficult for authorities to shut down or control. Users can access content on Freenet anonymously, and content is distributed dynamically across the network.
Anonymity and encryption on the dark web
- Anonymity: Anonymity is a fundamental aspect of it, allowing users to access content and interact with others without revealing their identities. This anonymity is achieved through the use of overlay networks like Tor, which obfuscate users’ IP addresses and encrypt their internet traffic.
- Encryption: Encryption plays a crucial role in ensuring the privacy and security of users on it. Communication and data transmission are encrypted end-to-end, preventing unauthorized access or surveillance by third parties. This encryption not only protects users’ identities but also safeguards sensitive information from interception or tampering.
Understanding how it operates on overlay networks like Tor, I2P, and Freenet provides insights into its unique architecture and the mechanisms that enable anonymity and privacy. In the next section, we will delve deeper into the implications of anonymity and encryption on it, including their impact on security and law enforcement efforts.
Difference between the Surface Web, Deep Web, and Dark Web
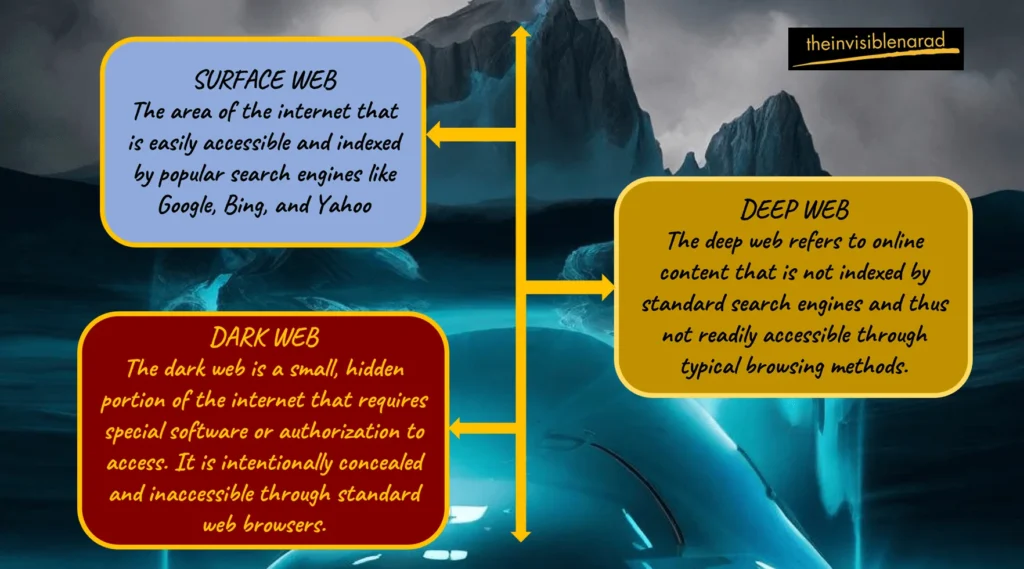
| Surface Web | Deep Web | Dark Web | |
|---|---|---|---|
| Definition | This part of the internet that is easily accessible and indexed by popular search engines like Google, Bing, and Yahoo is referred to as the surface web. Which is additionally referred to as the indexed web or visible web. | The deep web refers to online content that is not indexed by standard search engines and thus not readily accessible through typical browsing methods. | The dark web is a small, hidden portion of the internet that requires special software or authorization to access. It is intentionally concealed and inaccessible through standard web browsers. |
| Accessibility | Websites and web pages on the surface web can be accessed using conventional web browsers such as Chrome, Firefox, Safari, etc. | Accessing content on the deep web often requires specific permissions, authentication, or access to databases and private networks. | Accessing the dark web typically requires specialized software like Tor (The Onion Router), I2P (Invisible Internet Project), or Freenet. These tools anonymize users’ identities and obscure their online activities. |
| Content | Surface web content includes publicly available information, websites, blogs, forums, social media platforms, news sites, e-commerce stores, and more. | The deep web encompasses a vast array of content, including private databases, academic journals, subscription-based services, online banking, medical records, government resources, and other restricted or password-protected content. | The dark web is known for hosting a variety of illicit and anonymous activities, including illegal marketplaces, forums, hacking communities, whistleblowing platforms, and more. However, it also serves as a platform for individuals seeking privacy and anonymity for legitimate purposes, such as journalists, activists, and whistleblowers. |
| Examples | Websites like Wikipedia, CNN, Amazon, Facebook, and YouTube are all part of the surface web. | Password-protected websites, subscription-based content platforms, online banking portals, and academic databases are all part of the deep web. | Websites on the dark web often have addresses that end in “.onion” and may include illicit marketplaces like Silk Road (now defunct), forums like The Hidden Wiki, and platforms for anonymous communication and file sharing. |
Myths vs. Reality
Common misconceptions about the dark web
- Criminal Haven: One prevalent misconception is that it is solely a haven for criminal activities such as drug trafficking, weapons trading, and illegal hacking. While such activities do exist, they represent only a fraction of the content on it.
- Inaccessibility: Another myth is that accessing it is inherently illegal or dangerous. While there are risks associated with navigating this hidden network, merely visiting it does not constitute criminal behavior.
- Anonymity Guarantees Security: Many believe that the anonymity provided by it ensures complete security and privacy. However, users are still susceptible to various threats, including malware, scams, and law enforcement surveillance.
Dispelling myths with facts and examples
- Diverse Content: Contrary to popular belief, it hosts a wide range of content beyond illicit activities. It includes platforms for anonymous communication, whistleblower forums, privacy-focused marketplaces, and resources for individuals living under oppressive regimes.
- Law Enforcement Efforts: While it does facilitate criminal activities, law enforcement agencies actively monitor and prosecute offenders. High-profile cases, such as the takedown of Silk Road and other illicit marketplaces, demonstrate ongoing efforts to combat illegal behavior on it.
- Privacy Concerns: Despite its reputation for anonymity, the dark web poses significant privacy risks. Incidents of data breaches, identity theft, and malicious attacks underscore the importance of exercising caution and implementing security measures when navigating this hidden network.
Highlighting legitimate uses of the dark web
- Journalistic Integrity: It provides a platform for whistleblowers and journalists to share sensitive information securely, protecting both the source and the integrity of the information.
- Privacy Advocacy: Individuals concerned about online privacy and surveillance may utilize it to communicate anonymously, share resources, and advocate for privacy rights without fear of retribution.
- Academic Research: Researchers and academics may access specialized databases and resources on it for scholarly purposes, such as studying cybersecurity, cryptography, and emerging technologies.
While it is often associated with illicit activities and anonymity, it is essential to separate fact from fiction. By dispelling common myths and recognizing its legitimate uses, we can better understand the complexities of this hidden network and its implications for privacy, security, and freedom of expression.
Content on the Dark Web
Illegal Activities and Marketplaces
- Drug Trafficking: It hosts numerous illegal marketplaces where drugs of all kinds, including opioids, stimulants, and prescription medications, are bought and sold anonymously. Transactions typically occur using cryptocurrencies like Bitcoin to maintain anonymity.
- Weapons Trading: Illicit arms trafficking is prevalent on it, with vendors offering firearms, explosives, and other weapons for sale. These marketplaces cater to individuals seeking to acquire weapons illegally, bypassing legal restrictions and regulations.
- Stolen Data and Identity Theft: Its forums and marketplaces facilitate the sale of stolen data, including personal information, credit card numbers, and login credentials. This data is often obtained through hacking, phishing, or data breaches and is sold to individuals or groups for fraudulent purposes, such as identity theft or financial fraud.
Information and Data Exchange

- Whistleblowing Platforms: The dark web provides a platform for whistleblowers to share sensitive information securely and anonymously. Platforms like SecureDrop allow individuals to submit documents and tips to journalists and media organizations without revealing their identities, protecting both the source and the integrity of the information.
- Research and Academic Resources: Researchers and academics may access specialized databases and resources on it for scholarly purposes. These resources cover a wide range of topics, including cybersecurity, cryptography, privacy-enhancing technologies, and emerging fields of study.
- Privacy and Security Tools: It offers a variety of privacy and security tools, including encrypted messaging apps, VPN services, and anonymity networks like Tor. These tools help users protect their privacy and security online, mitigating the risk of surveillance, tracking, and censorship.
Dark Web Communities and Forums
- Discussion Forums: Dark web communities and forums provide a platform for individuals to engage in discussions on a wide range of topics, including technology, politics, philosophy, and more. These forums offer a degree of anonymity and privacy, allowing users to express themselves freely without fear of reprisal or censorship.
- Hacking and Cybersecurity: It is home to communities of hackers, cybersecurity professionals, and enthusiasts who exchange knowledge, tools, and techniques related to hacking, cyber-attacks, and digital security. While some discussions may be benign or educational, others may involve illegal activities or malicious intent.
- Support Groups and Counseling: It communities also serve as support groups for individuals facing various challenges, including mental health issues, addiction, and trauma. These forums provide a safe and anonymous space for individuals to seek advice, share experiences, and connect with others facing similar struggles.
The content on it is diverse and multifaceted, ranging from illegal activities and marketplaces to legitimate information exchange and community forums. While the dark web is often associated with illicit behavior, it also serves as a platform for privacy, free expression, and support for individuals navigating the complexities of the digital world.
Privacy and Security Concerns
Ethical implications of using the dark web
Anonymity vs. Accountability
It offers anonymity, allowing users to browse and communicate without revealing their identities. However, this anonymity can also enable unethical behavior, such as illegal activities and malicious actions, with little fear of accountability.
Freedom of Expression vs. Harmful Content
While the dark web provides a platform for free expression and privacy, it also hosts harmful content, including illegal marketplaces, extremist forums, and explicit material. Balancing the right to free speech with the need to protect users from harm presents ethical challenges.
Moral Responsibility
Users of the dark web must consider their moral responsibility when engaging with its content. Supporting illegal activities, participating in illicit transactions, or promoting harmful ideologies can have serious ethical implications.
Risks associated with accessing the dark web
- Malware and Cyber Attacks: The dark web is rife with malicious actors who distribute malware, phishing scams, and other cyber threats. Accessing suspicious websites or downloading files can expose users to malware infections and compromise their devices and personal information.
- Law Enforcement Surveillance: While anonymity is a defining feature of the dark web, users should be aware that law enforcement agencies actively monitor activity on these networks to combat illegal activities. Engaging in illicit behavior can result in legal consequences and law enforcement scrutiny.
- Financial Loss and Fraud: Dark web marketplaces often facilitate the sale of stolen data, counterfeit goods, and fraudulent services. Users risk financial loss and identity theft when participating in transactions on these platforms, as sellers may not deliver as promised, or buyers may fall victim to scams.
Protecting personal information and staying safe online
- Use Secure and Encrypted Tools: When accessing it, utilize secure and encrypted tools like the Tor browser and virtual private networks (VPNs) to protect your anonymity and data privacy.
- Practice Safe Browsing Habits: Avoid clicking on suspicious links, downloading unknown files, or engaging with untrustworthy websites. Exercise caution when interacting with strangers and conducting transactions online.
- Guard Personal Information: Refrain from sharing sensitive personal information, such as your real name, address, or financial details, on it. Limit the amount of information you disclose to minimize the risk of identity theft and fraud.
Addressing cybersecurity threats
- Employ Security Measures: Implement robust cybersecurity measures, such as antivirus software, firewalls, and regular software updates, to defend against malware and cyber-attacks.
- Educate Yourself: Stay informed about cybersecurity best practices and emerging threats to better protect yourself and your devices when accessing it or browsing online.
- Report Suspicious Activity: If you encounter illegal or harmful content on it, report it to the appropriate authorities or law enforcement agencies. By taking action, you can help combat illicit activities and promote a safer online environment.
While it offers privacy and anonymity, it also poses significant privacy and security risks. Users must navigate ethical considerations, protect their personal information, and mitigate cybersecurity threats to stay safe while accessing it.
Law Enforcement and the Dark Web

Efforts to Combat Criminal Activity on the Dark Web
Cybercrime Task Forces
Law enforcement agencies around the world have established specialized task forces dedicated to combating criminal activity on it. These task forces collaborate with international partners, cybersecurity experts, and intelligence agencies to investigate and disrupt illicit operations.
Covert Operations
Law enforcement agencies conduct covert operations to infiltrate dark web marketplaces, forums, and communities. Undercover agents may pose as buyers or sellers to gather intelligence, identify criminal networks, and gather evidence for prosecutions.
Targeted Takedowns
Law enforcement agencies coordinate targeted takedowns of illicit marketplaces and websites on the dark web. Through coordinated efforts involving legal action, server seizures, and domain takedowns, authorities aim to disrupt criminal operations and hold perpetrators accountable.
Challenges Faced by Law Enforcement Agencies
Anonymity and Encryption
The dark web’s anonymity and encryption technologies present significant challenges for law enforcement agencies. Criminals leverage these tools to evade detection and conceal their identities, making it difficult for authorities to track their activities and gather evidence.
Jurisdictional Issues
Since illegal activity can occur across national borders, law enforcement efforts become more difficult by the borderless nature of the internet and the dark web. For law enforcement agencies, coordinating investigations, exchanging intelligence, and extraditing criminals across international borders present logistical and legal obstacles.
Rapid Evolution of Technology
The rapid evolution of technology presents a constant challenge for law enforcement agencies, as criminals adapt their tactics and techniques to evade detection. Keeping pace with emerging threats, encryption methods, and anonymization tools requires ongoing training, resources, and collaboration with cybersecurity experts.
Cases of Success and Failure in Policing the Dark Web
Success Stories
Law enforcement agencies have achieved notable successes in policing the dark web, including the takedown of major illegal marketplaces like Silk Road, AlphaBay, and Hansa Market. These operations involved coordinated efforts, undercover investigations, and collaboration with international partners, resulting in arrests, prosecutions, and the seizure of illicit assets.
Challenges and Limitations
Despite successes, law enforcement agencies face challenges and limitations in policing the dark web. Criminals continuously adapt their tactics to evade detection, and the decentralized nature of the dark web makes it challenging to dismantle criminal networks entirely. Additionally, the proliferation of encrypted messaging platforms and privacy-enhancing technologies complicates investigations and surveillance efforts.
Lessons Learned
Law enforcement agencies must continuously learn from both successful operations and failures in policing the dark web. To effectively police the dark web and fight cybercrime in the digital age, it is imperative to balance privacy rights and law enforcement priorities while investing in technology, training, and international cooperation.
Law enforcement agencies face significant challenges in policing the dark web, including anonymity, jurisdictional issues, and rapid technological advancements. Successes in combating criminal activity on the dark web require coordinated efforts, international cooperation, and ongoing adaptation to emerging threats and technologies.
The Future of the Dark Web
Technological Advancements and Trends

- Enhanced Anonymity: Technological advancements in encryption and anonymization techniques are expected to further strengthen anonymity on the dark web. This may lead to increased privacy for legitimate users but could also pose challenges for law enforcement efforts to combat criminal activities.
- Decentralization: The decentralization of dark web infrastructure, facilitated by emerging technologies like blockchain and decentralized networks, may make it more resilient to takedowns and censorship. However, this decentralization could also empower criminals and make it harder for authorities to regulate or monitor illicit activities.
- Evolving Marketplaces: Dark web marketplaces are likely to continue evolving, adapting to technological changes and law enforcement efforts. New marketplaces may emerge, offering a wider range of illicit goods and services, while existing ones may implement enhanced security measures to protect against infiltration and shutdowns.
Impact of Regulatory Measures
- Increased Regulation: Governments and regulatory bodies may implement stricter regulations and surveillance measures to combat criminal activities on the dark web. This could include enhanced monitoring of internet traffic, stricter enforcement of cybersecurity laws, and increased cooperation between law enforcement agencies.
- Balancing Privacy and Security: Regulatory measures aimed at curbing criminal activities on the dark web must balance privacy rights with security concerns. Efforts to enhance cybersecurity and combat illegal activities should not infringe on individuals’ rights to privacy and freedom of expression.
- Global Cooperation: Addressing the challenges posed by the dark web requires international cooperation and collaboration among governments, law enforcement agencies, and tech companies. Shared intelligence, coordinated investigations, and cross-border legal frameworks are essential for combating transnational cybercrime effectively.
Potential Consequences for Society
- Socioeconomic Impact: The dark web’s continued existence and evolution could have significant socioeconomic consequences, affecting industries such as cybersecurity, law enforcement, and e-commerce. Efforts to regulate and combat criminal activities on the dark web may also impact internet freedom and innovation.
- Public Perception and Trust: Public perception of the dark web and its associated risks may influence trust in online platforms and digital technologies. Increased awareness of cybersecurity threats and responsible internet usage is essential for building trust and resilience in the digital ecosystem.
- Ethical Considerations: As technology advances and regulatory measures evolve, society must grapple with ethical considerations surrounding privacy, surveillance, and online freedom. Balancing individual rights with collective security interests will be critical in shaping the future of the dark web and its impact on society.
Conclusion & FAQs
The dark web presents a complex and evolving landscape, with technological advancements, regulatory measures, and societal implications shaping its future trajectory. While the dark web offers opportunities for privacy, anonymity, and free expression, users must exercise caution and responsibility when navigating its depths. Education and awareness are essential for understanding the risks and benefits associated with dark web usage.
The future of the dark web is uncertain, with potential implications for privacy, security, and societal norms. By addressing technological, regulatory, and ethical challenges, society can navigate the complexities of the dark web while promoting a safe, secure, and inclusive digital environment.
Frequently Asked Questions (FAQs)
What is the Dark Web?
The term “Dark Web” describes a portion of the internet that is purposefully concealed and unreachable using conventional web browsers. Users can enjoy privacy and anonymity by using overlay networks such as Freenet, Tor, and I2P.
Is it Legal to Access the Dark Web?
In the majority of nations, it is legal to access the Dark Web itself. On the other hand, the Dark Web is the scene of several illicit activities, including hacking and drug trafficking. Such behavior is prohibited by law and may have legal repercussions.
How do I Access the Dark Web?
To access the Dark Web, you need specialized software like the Tor browser, which routes your internet traffic through encrypted relays, masking your IP address. It’s important to note that accessing the Dark Web requires caution and awareness of potential risks.
What Potential hazards Associated with Accessing the Dark Web?
The Dark Web poses several risks, including exposure to malware, scams, illegal content, and surveillance. Users may encounter malicious actors seeking to steal personal information, engage in fraud, or distribute harmful content.
Can I Find Legal Content on the Dark Web?
While the Dark Web is often associated with illegal activities, it also hosts legitimate content and services. For example, whistleblowing platforms, privacy-focused forums, and academic resources can be found on the Dark Web. However, users should exercise caution and discernment when exploring.
How can I Stay Safe on the Dark Web?
To stay safe on the Dark Web, it’s essential to use secure and encrypted tools, practice safe browsing habits, and avoid sharing sensitive personal information. Additionally, being aware of potential risks and staying informed about cybersecurity best practices is crucial for protecting yourself online.

Normally I do not read article on blogs however I would like to say that this writeup very forced me to try and do so Your writing style has been amazed me Thanks quite great post.